Security Tools
YourSix goes to great lengths to ensure data is secure. As such, many features are offered within the Y6OS platform to ensure privacy.
Role-Based User Permissions:
Choose the perfect permission set for users based on the principle of least privilege to ensure no one has access to data they don’t need. Role-based access for users reduces the chance of unintentional changes to permissions, as well as exposure of data by restricting users to isolated features of the platform.
See User Management for more information.
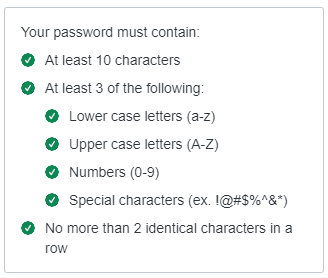
Password Requirements:
YourSixOS requires all users to create a complex password for each account. These requirements follow updated best practices put forth by the most trusted Information Security organizations.
Single Sign-On:
YourSixOS provides the option for each organization to activate Single Sign-on to further secure your company’s account.
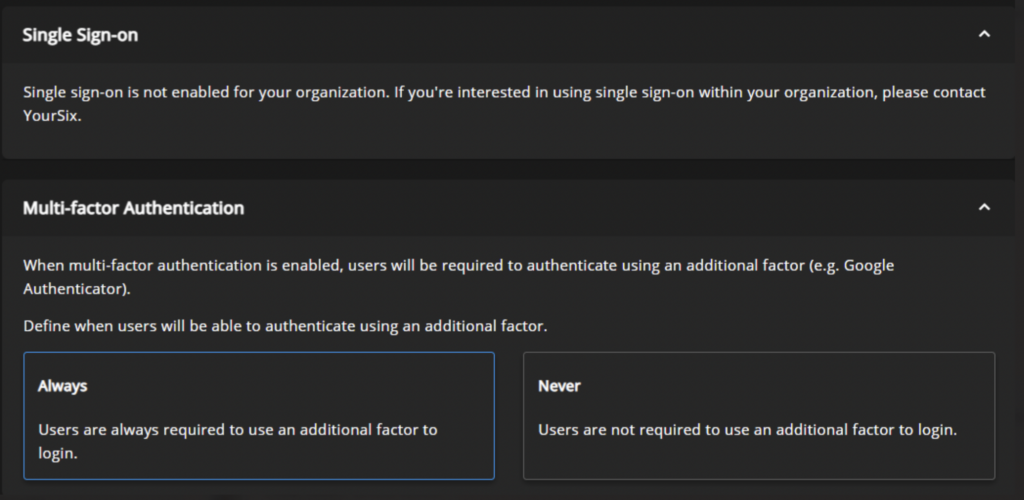
Multi-Factor Authentication:
YourSixOS integrates with multiple authentication applications, allowing customers to choose what works best for the situation. These applications provide one-time codes to ensure each login is secure from intruders through MFA (Multi-factor Authentication). MFA adds an extra layer of security by using secure, convenient, and cost-effective technology. If a password is compromised by an attacker, your account will still be protected when utilizing MFA.
High Availability:
YourSix partners with the best vendors in the business to ensure that video management and feeds are always up and running. Every service deployed is run in multiple availability zones.
Brute-Force Protection:
YourSix Authentication process recognizes brute force attempts at breaking login credentials and shuts them down immediately locking out potential attackers.
Suspicious IP Throttling:
Any time a single IP address is found to be rapidly attempting to create too many accounts or login attempts the YourSix platform will alert and intervene.
Breached Password Detection:
The Authentication server looks for hashes of passwords that have been leaked on the internet, or dark web as part of third-party breaches in the past and notifies users if a password being used has been compromised in any publicly known breaches.
Penetration Tested:
YourSix contracts with third-party penetration testers to ensure the platform is secure for users.
Security Proxy:
YourSix leverages a proxy at the edge of the cloud to verify all devices as they attempt connections to the platform.
Web Application Firewall:
A specific type of firewall is utilized to safeguard the platform from incoming web-based attacks on the site, or the infrastructure running it.
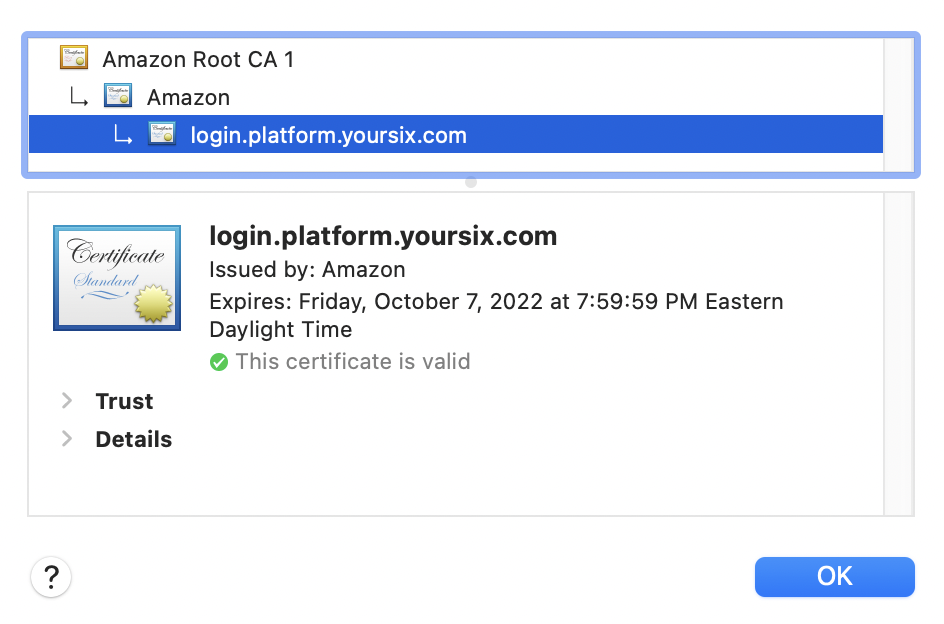
TLS Certificates:
Digital certificates are utilized in the authentication of the identity of a website and utilized to encrypt information sent to the server.
Data Encryption:
Data is encrypted both in transit and at rest to ensure confidentiality and integrity.
