Video Monitoring
In today’s security landscape, investing in a comprehensive cloud surveillance solution is essential for safeguarding your business. You’ve covered every corner of your premises with high-quality forensic evidence. But here’s a crucial question: When the doors are locked, your staff have left, and your facilities fall silent, who’s keeping watch?
To stay ahead in security technology, integrate advanced platforms like YourSixOS. Our system connects with professional monitoring companies and uses AI analytics to minimize false alarms, providing a comprehensive and responsive security solution.
By embracing next-gen technology and verification standards, you ensure that your business is not only protected but also prepared for the evolving landscape of security.
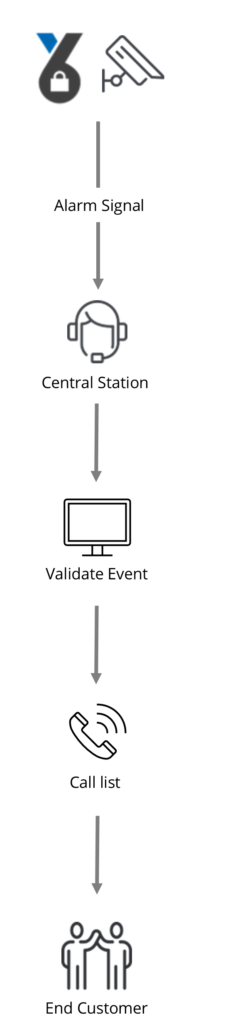 1. Event: The YourSixOS platform recognizes an event via an edge (on camera) AI analytic such as AOA (Axis Object Analytic)
1. Event: The YourSixOS platform recognizes an event via an edge (on camera) AI analytic such as AOA (Axis Object Analytic)
- Note: The device cannot determine the identity of the individual
2. Alarm Signal: An alarm signal is sent by the YourSixOS platform to the Central Station
- If a Device Group’s Alert state is in a “schedule” state (with the schedule active) or in an “Armed” state, then a signal will be sent to the Central Station
- No signal is sent if the state is in a “schedule” state with the schedule inactive or in an “Disarmed” state
- Signals are sent using notifications from Y6OS
- Note: The signal is triggered by an analytic which cannot decipher between individuals that should be there and those that should not (such as an intruder)
3.Central Station: Monitoring agent at the Central Station views the event and decides if the event is valid or a false alarm
- The monitoring agent does not decide if the event/individual is a threat or not. The monitoring agent does not identify the individual. Even if it is someone who is supposed to be at the location at that time, it is seen as a valid event.
4.Valid Event: If the event is found to be valid then the monitoring agent views the account notes, takes any action provided in the action plan, and begins to contact the customer based on the provided call list.
- Contacting law enforcement: The ability for the monitoring agent to contact law enforcement is dependent on state and local legislation. Customers are responsible for obtaining any permits/permission/registrations required by state/local law
5.Customer Call: Customer receives call from monitoring agent
- If the event is a false alarm, then the contact must provide the agent with their password for the agent to dismiss the event
- In areas where contacting law enforcement is limited, it will be the customer’s responsibility to reach out to law enforcement after the monitoring agent has made contact with them.
Event Uploader
The event uploader ensures you don’t miss critical events during unexpected internet outages. Once the outage is resolved, both the event and notification are swiftly transmitted. This means that any events occurring during the outage will be sent as soon as the connection is restored. When combined with edge storage on an SD card, this guarantees that you receive event notifications and have the footage readily available for review. This unique feature, not commonly supported in the industry, is a key differentiator that sets the YourSix solution apart.
Reducing False Alarms
False alarms can waste valuable time, strain resources, and erode confidence in your security system. At YourSix, we believe video monitoring should deliver clarity—not be clouded by false triggers from shadows, weather, or wildlife. Explore the recommendations located here (Reducing False Alarms) for effective strategies and best practices to significantly reduce false alarms using the YourSixOS platform.
Central Station Software Partners
YourSix facilitates video monitoring by integrating with top central station software, empowering central stations to carry out their monitoring tasks effectively.

