Access Control Configuration
This page contains basic recommendations for configuring a controller, barrier, and access rule in YourSixOS. For hardware instructions, please consult the vendor’s hardware manuals and guides. Additionally, it is the installation partner’s responsibility to comply with all life safety codes.
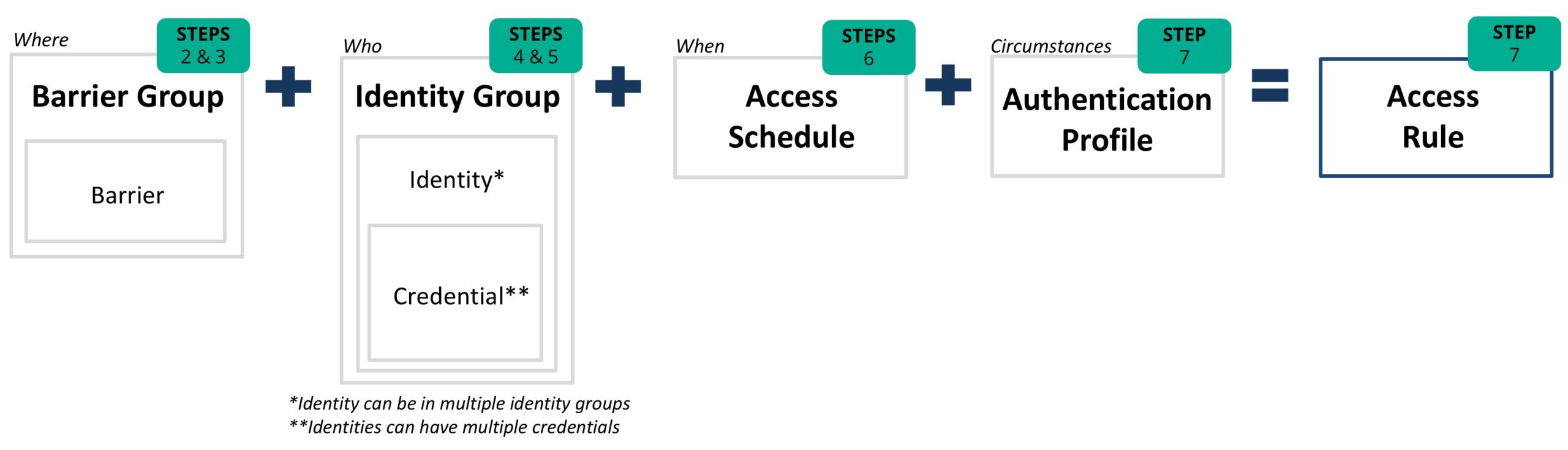
Y6OS Access Control defines who is allowed to enter, where, when, and under what conditions. To configure this, an authorized user will follow a series of steps. The process concludes with the creation of access rules, which are the result of the preceding elements, including barriers, barrier groups, identities, identity groups, and access schedules.
Please refer to the platform guides or Access Control Training Videos for more details on each step
Basic Steps for Access Control Setup
-
-
- Add Controller (Must be completed by the integrator)
- Add Barriers + Configure Barriers (Must be completed by the integrator)
- Add Barrier Groups
- Add Identities + Add credentials
- Add Identity Groups
- Add Access Schedules
- Add Access Rules
-
Illustration of Access Control Procedures Leading to the Formation of an Access Rule